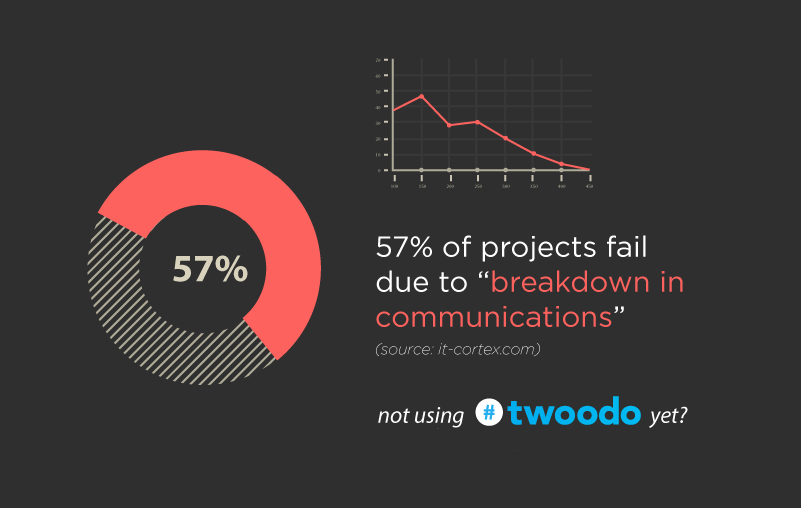
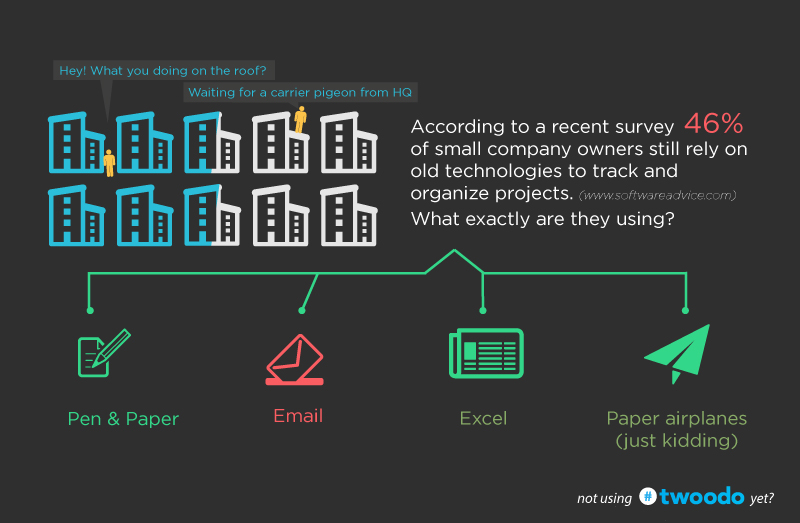
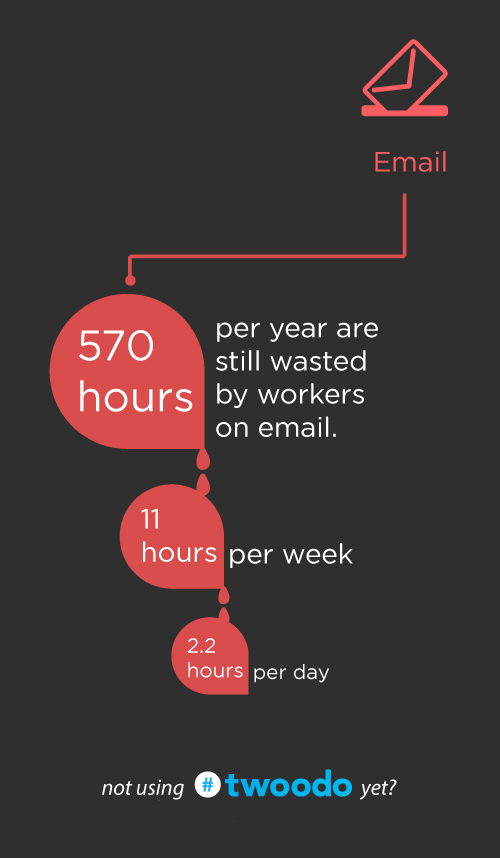
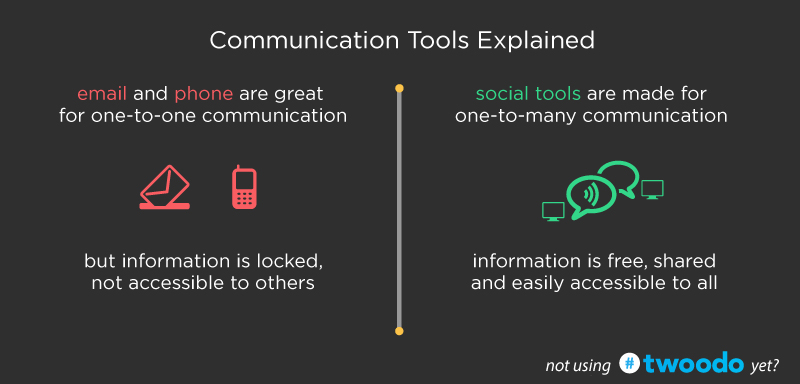
Unless you do your job exclusively via email, there’s no excuse for you to have that tab or app open. There I said it..
But you do have it open most of the time, right? It’s hard to ignore. Suddenly you see the Inbox (1) in bold appear and you rush to see what it is. And it’s never a game changing message. But the micro-second between seeing it and comprehending it gives us a rush, and that rush becomes addictive. Email is an important medium of communication, indisputably. However, constant interruptions (let’s say every 30 seconds to 15 minutes) do not allow our minds to focus on a task at hand. Without focus, errors are more likely. Silly slip-ups that leave you banging your head against the wall and sending out a flurry of apologies. Or, it can result in serious accidents and poor decision-making with huge consequences. This is why disciplining ourselves on how to manage email is so important.
“…a three-second distraction can double the number of mistakes people make” - Live Science
But “priorities” doesn’t just mean your job. With smartphones, laptops and tablets hanging around the home - and with many public places now supplying free wifi - it’s easier than ever for our brains to get it’s fix of email-checking. We are wasting our precious time all the time. And on what? Why do we give more attention to apps and videos than to our loved ones or to our own self improvement?
Why do we check our inboxes so often?
Psychology Today goes into more detail here on the points they believe are why we crave checking our inboxes so much.
1. Connecting to other people
Many tasks are solitary. Sure, there are meetings, but once your task is assigned you must go to your corner and get it done. If it is a time-consuming task this means long stretches of time alone. Despite our assertions of being able to work independently, we require human communication at intervals. The email inbox provides relief, but it’s overkill. Do you give a child a single candy, or do you leave a bowl of candy within arm’s reach? It’s irresistible to all but the most focused.
2. Respite from a difficult task
Knowledge work is becoming a larger and larger portion of white-collar jobs. And knowledge work requires more brainpower, more creativity. This can lead to the mind feeling exhausted faster than a repeated task job. So, we find relief by looking at our email, or notifications on our phones and social media. It’s the mental equivalent of taking a breather after doing 10 lengths of the swimming pool.
3. Changing it up
When you are stuck, it’s good to do something else for a while until inspiration strikes again. This is especially so with tasks that require creativity. Unfortunately, instead of changing over to another worthwhile task, we waste time on trivial email. The ideal solution would be to have two projects on the go so that you could switch between the two when roadblocks are encountered in one. I personally found that freelancing a few hours a week with another company gave me a fresh perspective on working on my startup. And having your own startup is one of the most totally immersing things around!
4. Distractions make us feel better and are therefore addictive
Even if distractions don’t end in real results, it’s good to feel busy. It’s also good to feel noticed. Psychology Today states that you get addicted to email and notifications because of the low but regular feelings of worth, as opposed to the irregular but massive (by comparison) rewards of completing a challenging or long task. Self-discipline is not easy and technology has made it even harder. Multi-tasking, interruptions and distractions arguably make us more stupid. Our mental energy is spent trying to remember where we were in a task and getting back into it, rather than reaching a deeper state of concentration and insight that comes from focusing.
Email makes you focus on…
- trivial newsletters
- notifications
- invitations to webinars, hangouts
- updates of services you subscribe to
- requests that are not the highest priority
“More generally, email puts you in response mode, where you are doing what other people want you to do, rather than send mode, where you are deciding what you want to do and taking action.” - Anne-Marie Slaughter, Princeton
Would there really be a life-or-death scenario if you didn’t check in more than once an hour? Alright, I’ll admit that once I lost a bid on an apartment rental… but that’s as serious as it’s gotten. Being overwhelmed by info, and being used to it, all day long has mental health consequences. Erin Anderssen wrote this excellent in-depth overview of the war for our attention by technology. Not surprisingly, as we check our email and notifications for the tenth time in the day and nothing is there - anxiety and depression lurk in the background. You may not even notice it. Being contacted makes us feel important, even if the contact is automated or unimportant. Eventually, NOT being contacted has the opposite psychological effect. She quotes Linda Stone - that perhaps we need to talk about “attention management” rather than “time management”. We’ve even developed “interruption science” which studies the effects of disruptions on job performance. And the guilty party is… “NOTIFICATIONS!” 
It’s that bad. There’s no shame in wanting to be connected, to take a mental break, to add variety to our day. But whilst we over-engage in the trivial, real life is passing us by. Are people at music festivals who spend their time uploading photos and videos of the event really enjoying the moment with friends? Time is precious. Use it to create and add value rather than get bloated on information we’ll never need.
How to manage email
#1: Batch your time
Cal Newport, in an article for 99U, describes how he applied the most commonly-cited solution (batching your time) to a workday. This involves breaking your time into 30 minute batches of either one long task or a bunch of short tasks. If you decide to check an email, you are required to spend a full half an hour on short tasks. It’s all or nothing. “…if you survive the annoyance, there’s also no avoiding the reality that your work will be of a much higher quality” So, the payoff is the difficulty of arranging the times when you can look at email versus better results in your larger, more important projects at the end of the day. Not a bad trade if you can stick to it. But most people can’t handle the inconvenience.
#2: Check email/notifications at a specific time, for example 5 minutes once an hour
This plan offers more flexibility and freedom than the half-hour batching BUT the temptation is to go over the time limit. So, for example, if you end up spending 20 minutes on email in this hour then you miss your 10 minute stint in the following hour. Basically, the aim is to spend no more than 10 minutes per working hour, i.e. 80/90 minutes per day on email. If you think that is still excessive (it is almost 20% of your work day) reduce it to 5 minute blocks.
#3: Do a major email blast first thing in the day, and once in the afternoon
This is the nuclear option, some would say! Check, organize and reply to all your email at 9am and at 2pm. No matter how long it takes! And under no circumstances can you check in between those times. You can orient your contacts to this new system by including it as an email signature (due to email overload, all email will be responded to at the following times…). You can arrange to have your closest collaborators call you if something extremely important comes up. If there are contacts that are ALWAYS urgent, set up a “red alert” system only for these contacts.
#4: Don’t have an email address
Hmmm. I hate to say “impossible”…